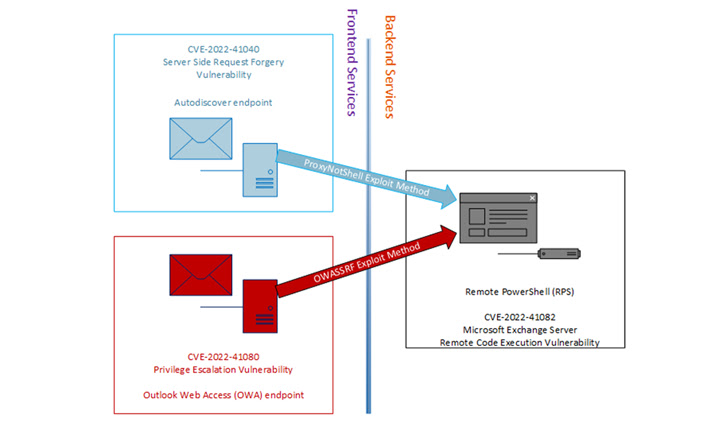
Threat actors affiliated with a ransomware variant called Play use a never-before-seen exploit chain that blocks the ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) via [1] Outlook Web Access ( OWA) bypasses. Brian Pitchford, Erik Iker, and Nicolas Zilio, researchers at CrowdStrike, said in a technical report published on Tuesday, December 20, 2022[2]: “This new exploit exploits URL rewriting inhibitors[3] for endpoint [4] Bypasses Autodiscover. The Play ransomware, which first appeared in June 2022, [5] has been shown to adopt many of the tactics employed by other ransomware families such as [6] Hive and [7] Nokoyawa, the latter in September 2022 upgraded to Rust[8]. A cybersecurity firm's investigations into several Play ransomware intrusions revealed that initial access to target environments was not achieved by exploiting CVE-2022-41040[9] directly, but through the OWA endpoint. This technique, called OWASSRF, is likely to use another critical flaw tracked as [10]CVE-2022-41080 (score 8.8 on the CVSS scale) to achieve the score increase, followed by [11]CVE- 2022-41082 uses remote code execution. Play It's worth noting that both CVE-2022-41040 and CVE-2022-41080 stem from a server-side request forgery (SSRF[12]) case that allows an attacker to access unauthorized internal resources, in this case a remote service PowerShell to access [13]. CrowdStrike said successful initial access would allow an adversary to remove legitimate Plink and AnyDesk executables to maintain permanent access, as well as take steps to clean up Windows event logs on infected servers to hide malicious activity. All three vulnerabilities were addressed by Microsoft as part of Patch Tuesday updates for November 2022[14]. However, it is unclear whether CVE-2022-41080 was exploited as a zero-day flaw alongside CVE-2022-41040 and CVE-2022-41082. The Windows maker, in turn, has labeled CVE-2022-41080 with a "highly exploitable" rating, meaning an attacker could create exploitable code that could reliably exploit the flaw. CrowdStrike also noted that a proof-of-claim (PoC) Python script discovered and leaked last week by Huntress Lab researcher Dray Agha[15] may have been used by Play ransomware actors to gain early access. This is evidenced by the fact that running a Python script made it possible to "reproduce reports generated in recent Play ransomware attacks." "Organizations should apply the November 8, 2022 patches for Exchange to prevent the exploit, as URL rewriting inhibitors for ProxyNotShell are not effective against this exploit method," the researchers said. Update Cyber security firm Rapid7, in a related report on Wednesday, December 21, 2022, announced that it has observed "an increase in the number of Microsoft Exchange server vulnerabilities" through the OWASSRF exploit chain for remote code execution. Rapid7 researcher Glenn Thorpe noted[16]: "Patched servers do not appear to be vulnerable, servers using only Microsoft's blockers appear to be vulnerable". Threat actors use this issue to deploy ransomware. "The reported method exploits vulnerable systems that have not applied our latest security updates," a Microsoft spokesperson said in a statement shared with The Hacker News, adding, "Customers should install the latest updates, specifically the November 2022 updates for [17 [Prioritize Exchange Server]. Those interested in this field are invited to send their articles to the website of this magazine.